No new research was conducted this week due to finals.
22 Apr – 28 Apr
As the semester nears it’s end, the group met this week to discuss our plans for the summer and how we intend to write our final report. Though the direction of the project took some turns and we do not have actual results , we still have a lot of things to discuss in our report. I learned so much while being a part of this CREU research group and truly enjoyed the experience. I was introduced to machine learning, gained experience in artificial intelligence and dabbled in some cybersecurity topics as well. Hopefully, I am able to continue CREU research next year.
As for our summer plans, each of us will be going our separate ways. Samantha has an internship in Virginia. Dr. Bhattacharya will also be doing research in Virginia and I will be back at the Aberdeen Proving Ground Army Research Lab. Catherine may be there as well.
After summer I will be returning to Fayetteville State to complete my BS in Computer Science. Samantha is transferring to NC State to complete a Computer Engineering degree. Catherine graduates this May, so she will either go to graduate school or go straight into the work force. Either way, I am sure she will will be successful. She is truly one of the most talented student in our curriculum.
I am unsure of my plans following graduation this fall. I absolutely want to go to graduate school but am undecided if I want to go right away. I have the summer to think about this further and come to a decision.
15 Apr – 21 Apr
This week we were unable to have our weekly meeting because Dr. Bhattacharya, Catherine, Samantha and the rest of our Swarmathon group were in Florida for the NASA Swarmathon competition. I unfortunately was unable to attend but I kept tabs on the teams’ progress via group chat. Though we did not win, I am proud of all of our effort as a team.
While the team was in Florida I continued to review the honeypot project and learn some of the software and packages that were used. Anum is a low interaction honeypot that listens on several ports and records connections to those ports. I had never heard of this tool but it was very handy in tracking the movements of the attacker. Another method of tracking was conducted by GeoLite2, which was used to perform traffic analysis. In the code, you can also see the methods that were used to detect what the attacker was searching for. This project encourages me to continue to do research into to cybersecurity. I hope to continue training and possibly earn some certifications. To gain the skills to perform tasks such as identifying origins of attacks and set traps to lure the attackers in, would be very useful, not to mention exciting. I plan to look into getting some of these certifications.
8 Apr – 14 Apr
This week Fayetteville State University hosted a Department of Defense conference called “Taking the Pentagon to the People.” Other than seeing some of my fellow classmates I seen some familiar faces from both the Thurgood Marshall College Fund Foundation and the Aberdeen Proving Ground Army Research Lab. I spent some time talking to Dr. Collins, whom I met last summer during my internship at Aberdeen ARL. I look forward to spending this summer in Aberdeen and beginning a new research project in machine learning.
Dr. Bhattacharya received an award for the CRA-W Protein Folding research project. Samantha, Catherine and I were recognized as well.
Next week is a big week for the Swarmathon group. The team will be flying to the Kennedy Space Center. Sadly I am unable to attend the competition but I will be cheering my teammates on from home!
1 Apr – 7 Apr
In this week’s meeting we continued to discuss the data from the secrepo website. Dr. Bhattacharya discovered how honeypots were being used as bait to entice potential attackers and gather information about them i.e. time of attack, sites visited, reason for and origin of attack. By implementing these honeypots, they purposely allow the attackers access to the server in order unveil the their intent, then possibly redirect them and even send malicious software to the origin of the attack. This is a rather bold approach because you run the risk of the attacker outsmarting the trap and finding their way around it resulting in a great deal of information being made available to the attacker; leaving your entire system vulnerable.
I am very excited about the direction of this project because I have always had a deep interest in cybersecurity. I have basic knowledge on cybersecurity topics but have never worked with actual data. We are to download all necessary packages, run the codes on Jupiter notebook and see if we can get answers to some of the questions presented on the website while swimming through the information given. As I continue to analyze the data, I will soon update this blog entry with my findings.
.
25 Mar – 31 Mar
Hello readers,
This week Dr. Bhattarya held a department seminar about machine learning from multi-modal data. In his talk he described how multi-modal data is used to solve many real world problems. He also discussed Convolutional Neural Network (CNN) and long-short term memory (LSTM) networks. I have some experience in research in regards to CNN so I was able to follow along through many discussion points. He also discussed image/video surveillance and machine recognition.
Following the talk, we held our CREU meeting where Dr. Bhattacharya had us take a closer look at some of the files from the SecRepo.com – Samples of Security Related Data website. Many of the files consisted of data that were not labeled, therefore they cannot be used in our research. After further investigation, we discovered a set of files that were labeled attack and non attack from a DARPA Intrusion Detection Evaluations conducted between 1998-2000. These data sets consist of bsm configuration files and raw data from simulations. Though there were a few files I was able to open, there are some that I cannot access due to the formatting of the files and possibly due to some provisions. I downloaded applications in efforts to open some of the bsm files but my attempts remained unsuccessful.
What I gathered from the files that I was able to open is that, many different attacks were attempted, mostly through telnet and smtp but I cannot gather whether or not these attempts were successful or not. My goal this week is to continue to study these files and hopefully find a way to open the files I had difficulties with and study those files as well.
18 Mar – 24 Mar
Since our Swarmathon code submission deadline was on the 19th and both the technical and Outreach reports being due on the 25th, most of this week was spent ensuring that those tasks were complete. I wrote my efforts to get the rovers to community by implanting the publisher/subscriber method. We were able to meet this Thursday and discuss our plan in reference to our research. As we continue to work with the Bro software Samantha and I have also been tasked with searching for conferences where we can present our research and findings. In efforts to truly understand the software we are now working with data in efforts to grasp how Bro Log is generating results, describe what it does and understand the data set and features.
11 Mar – 17 Mar
This week we were on spring break. No research or meeting conducted this week.
4 Mar – 10 Mar
Hello readers! This week I done some research on the Bro software. A week ago, I had never heard of Bro. While reading some background information on Bro, I was surprised to see that their history went back as far as it did. Vern Paxson, researcher at the Lawrence Berkeley National Laboratory (LBNL), designed and implemented the initial version of the software in 1995.
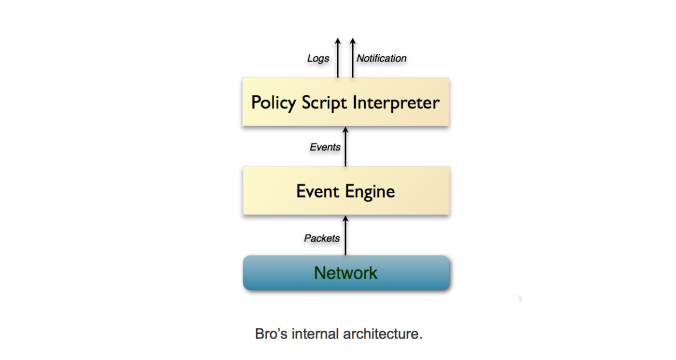
Below is a look at Bro’s architecture. As you can see Bro consists of two major components. The event engine and the script interpreter. The job of the event engine is to explore the incoming network activity and describe the incoming packets. It must identify what it has seen and if the data is of any significance. The policy script interpreter layer is responsible for executing a sequence of events that are written in Bro’s own scripting language. It decides what actions are to be taken on these incoming packets. With the Bro’s scripting language, real-time alerts can be generated and actions can be taken to activate a real-time response to incoming attacks. Thoroughly understanding how these layers work will be imperative as we move forward with our work.
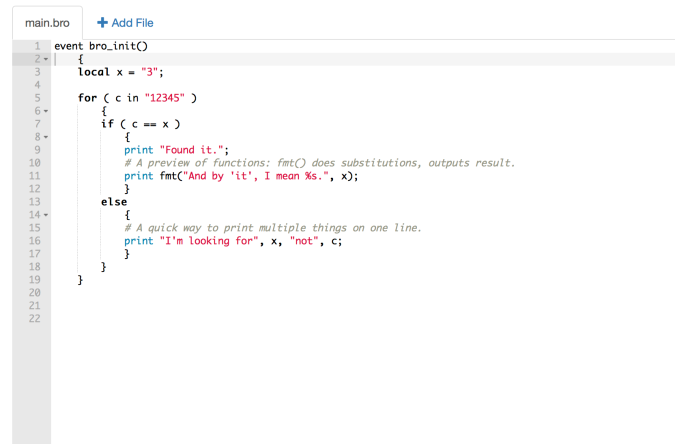
After discovering there was a Bro scripting language, I decided to explore the language a bit to see if it resembles any languages that I am familiar with. Below is an example of an if/else statement written in Bro from the Bro tutorial site. This if/else statement doesn’t seem difficult to understand but as I glanced a bit further into the tutorial, things start to get a bit confusing. Next week is spring break so I will have time to dive a little deeper into this tutorial.
Aside from having its own scripting language, Bro is also equipped with many other features i.e. interfacing, deployment and analysis. In the upcoming weeks, I will explore all features and get more practice with learning the scripting language.
25 Feb – 3 Mar
Another week complete. This week Catherine, Samantha and I met with Dr. Bhattacharya this Thursday to discuss the next phase of our research. Due to the ARL shifting their focus in their work to network traffic, we will be slightly shifting our focus as well. This will be a good extension of work with ML tools used and datasets collected by Bro software. None of us are familiar with Bro at all. We have been tasked with examining and understanding how to use the software We were also given some data we must sort through and attempt to identify what each file is and determine what is the signature for an attack.
Bro is a powerful network analysis framework, which by default churns out ASCII logs in a easily parseable whitespace separated format from network traffic, live or packet capture.
As far as the progress with the Swarmathon team, we are still having some hardware issues but are working through them as best as we can. I was given a great approach to take in efforts to get the rovers to communicate and share the same map. I will continue to focus on that area of the project. The final submission date is approaching, we have a lot of work to do but with all of us working diligently I am confident we will come up with something great.
I got some good news this week in reference to a summer internship opportunity. I applied to several internships and received offer letters from a few. I decided I will go back to the ARL in Aberdeen, MD. They have put together a project for me that focuses on the development of AI & ML based adaptive computing functions for heterogeneous computing environments. I will be using both Python and Java programming languages. I am very excited and looking forward to working with my mentor again and continue to gain experience and growth in areas I find of interest.
Short term goal: Examine Bro, work with examples and discover the pros and cons of using the software and how it can help with out project
Long term goal: ongoing